How i was able to hack NASA

Hello everyone! I am Yashwanth, a security researcher and bug bounty hunter. Recently, I found a PII (Personally Identifiable Information) Exposure vulnerability in a target and had my report accepted. I want to share my journey with you, as a bug hunter every hacker has a dream to hack a NASA and get into the hall of fame of nasa vdp and that dream makes me to the success of finding the vulnerability. #nasahacker😁

This is my first accepted bug report after encountering many duplicates. As a bug hunter, facing duplicates is common at the beginning. I struggled to find unique bugs but learned from others methodologies. Unfortunately, I kept encountering duplicates for about a month. I realized I needed to change my approach because publicly available methodologies are often followed by many bug hunters. To find vulnerabilities, I had to develop my own unique methods. This change in strategy recently led to my success.
I chose a target under the Vulnerability Disclosure Program (VDP), which doesn't offer bounties for findings. However, I was amazed by the tokens of appreciation they provide, as seen in others LinkedIn posts. This inspired me to find bugs. It's incredibly rewarding for a bug hunter to have their findings validated by the program. 😎
Now i was ready with my laptop and coffee and motivated to start hunt on the target, I began with a recon like gathering the subdomains and checking each and every possible ways of finding vulnerabilties, and it took 3 days initial phase to get the information like checking the technologies and took 1 week, 2 weeks 3 weeks and more over weeks passed without finding anything vulnerable site, i started to feel demotivated and discouraged.

i felt sad and kept the laptop iside for a while and took a nap, after getting up from the nap,i was thinking not to give up on the target, i took my phone and saw the notification came from the medium article as "how i was able to find the pii exposure vulnerabiltiy" i started reading the article and got the idea to find it, this time i got the vulnerable site and guess what, instead of PII Exposure i found a reflected XSS, i was so happy in that time.

i quickly started to writing the report and submitted the vulerablity.
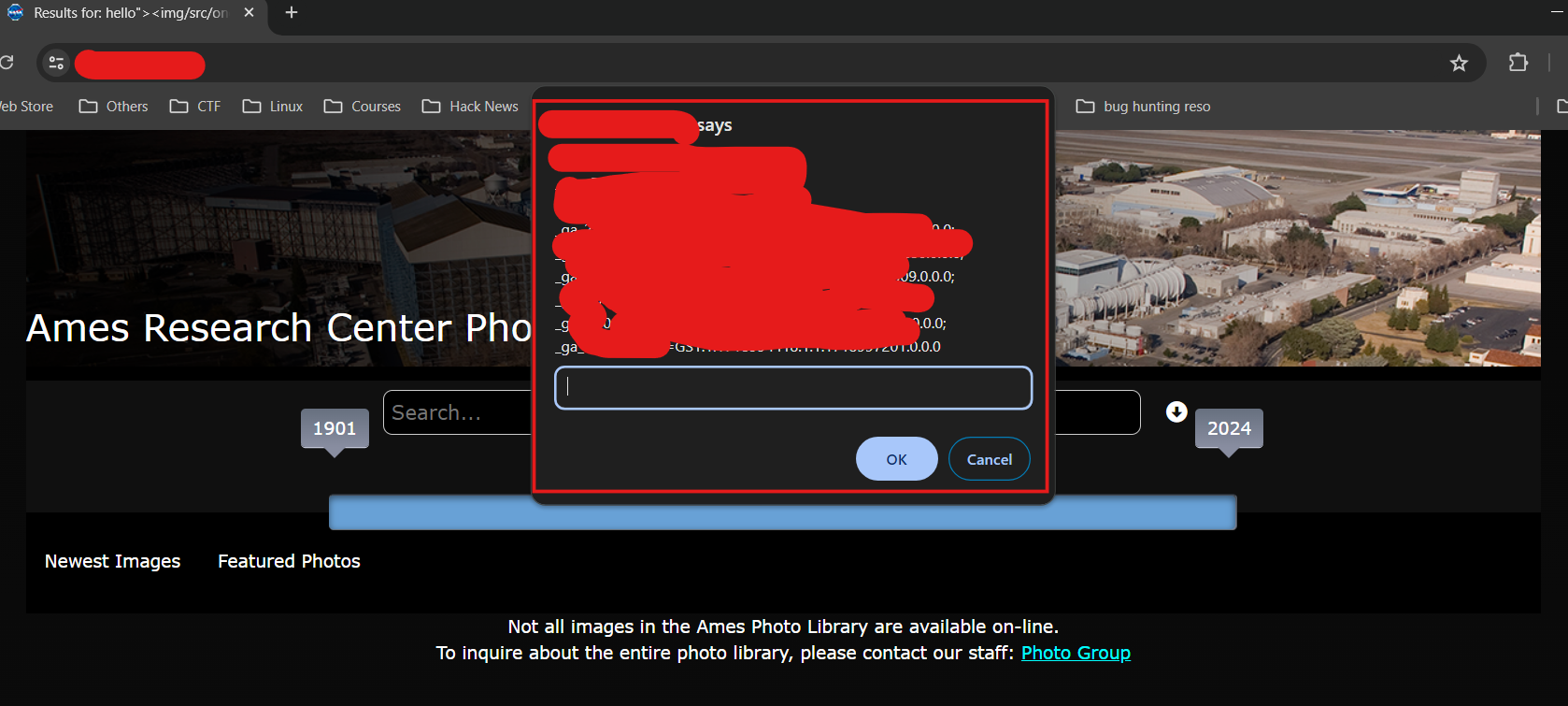
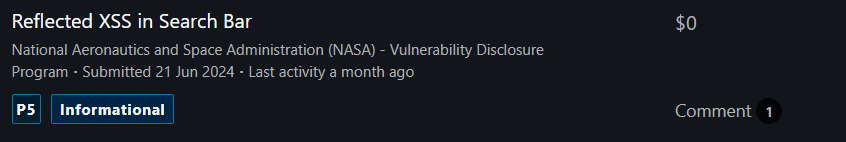
after few days passed i got the email called your report got informational- p5 and that time i felt come one man whats this........
After reviewing the report i got to know that i only effecting from it no other can have that RXSS, the reason behind that is, they already senitized the urls to not to inject payloads.☹️
Again i felt demotivated but this time i did not give up.
i started again hunting for it but after few days passed i found some suspicious files available through path i discoverd by the directory fuzzing which disclosing the personal information and dockerfile in public without login but removing the path it asking for a login, i felt happy again i found a vulerability in the target but this time i was checking for more in deep what we can do about it, after researching or checking got that someone got traige for the dockefile and PII exposure leaks in hackerone report.
i quickly started to writing the report and explaining about what we can do with it. guess what i got accepted. that time i felt literally so happy that days and nights struggling finally give something a satisfaction to me.

Reported date: 22 Jun 2024 12:05:22 UTC
triaged : 22 Jun 2024 12:41:04 UTC
got the first response from the team 22 Jun 2024 12:41:09 UTC as
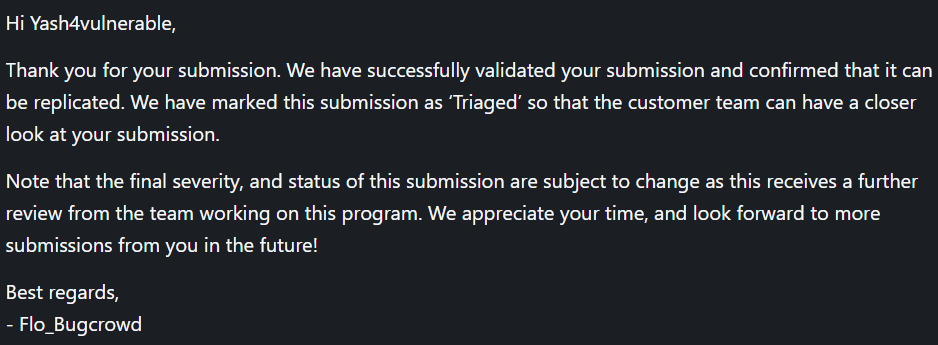
accepted by team: 01 Jul 2024 17:49:29 UTC
resolved by team: 18 Jul 2024 17:18:19 UTC
and got this tokens of appreciation from NASA

Stay persistent and keep learning from each attempt.
Good luck, and happy hunting!

