Learn About Google Dork

Google Dork, commonly known as "Google Hacking," is a method for using Google search to uncover security flaws in a website. Security researchers will find it quite useful, and you may obtain sensitive data, including usernames and passwords, by exploiting Google's web crawling capabilities.
Google Dorks are search terms that can lead to certain content on the internet, but they should only be used sensibly and morally. This is an illustration of how hackers utilize Google Dorks passwords to obtain private data from particular websites.
- **“inurl: domain/” “additional dorks**
A hacker would use the desired parameters as follows:
- inurl = the URL of a site you want to query
- domain = the domain for the site
- dorks = the sub-fields and parameters that a hacker wants to scan

Structure of Query Operators
Google Dorking query operators have a structure similar to regular Google search query operators. This technique involves using advanced operators and search queries to uncover information that is not typically available through regular searches.
The general structure of query operators in Google Dorking includes three elements:
1. Operator: A specific keyword or symbol that instructs Google what to search for. For instance, the “inurl” operator searches for pages that contain a particular keyword in their URL.
2. Keyword: The search term or phrase that you want to find. If you are looking for a specific password file, then “password” is your keyword.
3. Modifier: An additional search parameter that you can use to further refine your search. For example, the “filetype” modifier searches for a specific file type, such as a PDF.
Some of the Example google dorks:
- Intitle operator
The “intitle” operator searches for web pages with specific words or phrases in the title tag. For instance, if you’re looking for pages that contain the phrase “password” and have “index of” in the title, you would use the search term:intitle:”index of” password
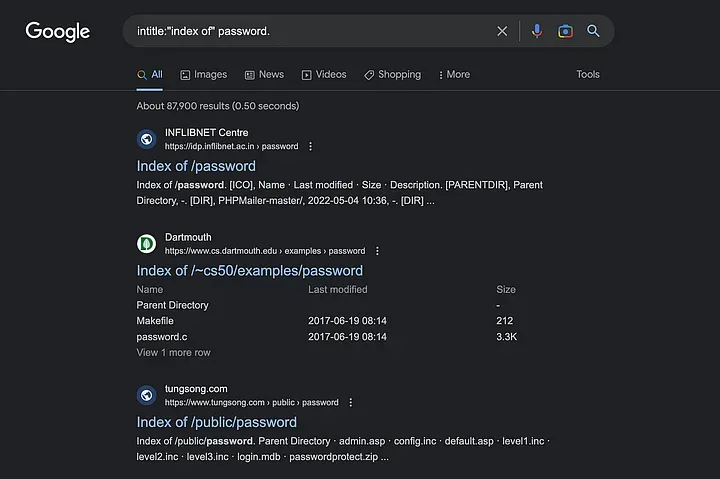
- Inurl operator
The “inurl” operator searches for web pages that contain specific words or phrases in the URL. For example, if you’re looking for pages that contain “admin.php” in the URL, you would use the search term: inurl:admin.php.
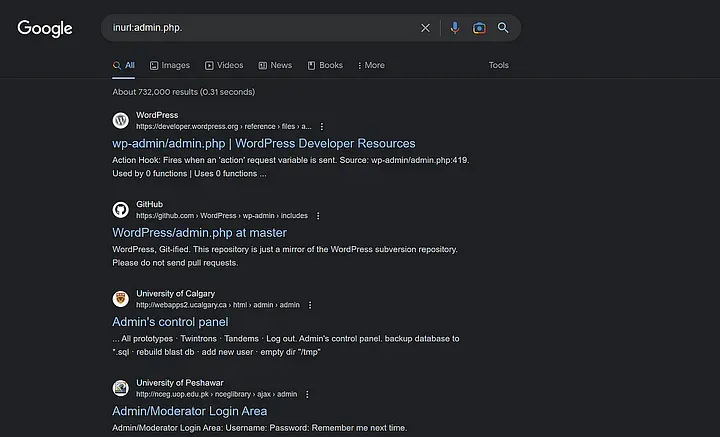
- Site operator
The “site” operator allows you to search within a specific website or domain. For instance, if you’re looking for pages on the example.com domain that contain the word “Steganography”, you would use the search term: site:yeahhub.com “Steganography”
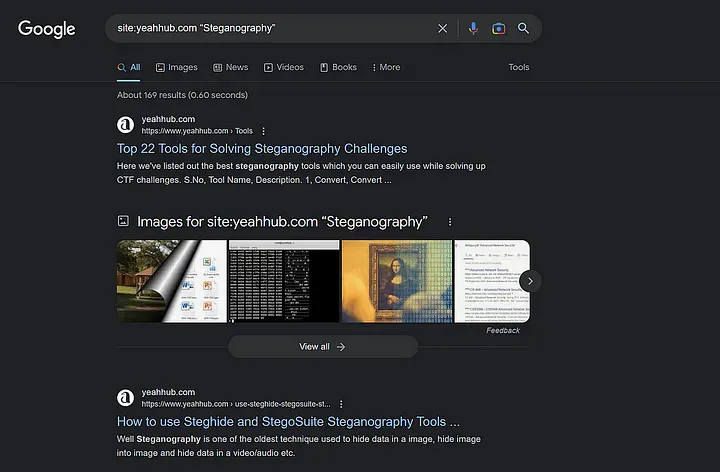
- Filetype operator
The “filetype” operator allows you to search for specific file types, such as PDFs or Word documents. For example, if you’re looking for PDF files that contain the phrase “confidential report”, you would use the search term:filetype:pdf “Advanced Network Security”
- Intext operator
The “intext” operator searches for pages that contain specific words or phrases within the body of the page. For instance, if you’re looking for pages that contain both the words “login” and “password” within the body of the page, you would use the search term: intext:”about” contact.
- Link operator
The “link” operator searches for web pages that link to a specific URL. For example, if you’re looking for web pages that link to the example.com domain, you would use the search term🔗”example.com”
- Cache operator
The “cache” operator is used to retrieve the cached version of a web page. When you search for a website using Google, Google creates a cached version of that page in its system. This version can be useful if the original website is temporarily down or if you want to view an older version of the website.
Here is the syntax to find the cached version of yahoo.com.cache:https://www.yahoo.com
- Related operator
The “related” operator is used to find web pages that are related to a specific URL. Here is the syntax to use the “related” operator to find sites similar to yahoo.com.
Main Purpose of Google Dorks :
Google Dorks can be used for a number of tasks, such as penetration testing, information collection, and website vulnerability evaluation.Through the use of focused keywords and particular search operators, you can narrow down your search to locate particular kinds of data or identify potential security holes on webpages. Information retrieval, vulnerability evaluation, and security testing are the main goals of Google Dorks. The following are some typical uses for Google Dorks:
- Information gathering: Google Dorks can gather precise information about a target, such as finding exposed directories, leaked documents, or sensitive files that search engines may inadvertently index.
- Website vulnerability assessment: Google Dorks can help identify potential website vulnerabilities by searching for specific file types, directory structures, or default pages that may reveal sensitive information or indicate weak security configurations.
- Penetration testing: Security professionals and ethical hackers use Google Dorks during penetration testing to discover potential entry points or vulnerabilities in a target’s web infrastructure.
- Security research: Researchers and security analysts may use it to investigate and uncover security flaws, data breaches, or other vulnerabilities present on the internet.
Google Dorks for Bug Bounty
A list of Google Dorks for Bug Bounty, Web Application Security, and Pentesting
Broad domain search w/ negative search
site:example.com -www -shop -share -ir -mfa
PHP extension w/ parameters
site:example.com ext:php inurl:?
API Endpoints
site:example[.]com inurl:api | site:*/rest | site:*/v1 | site:*/v2 | site:*/v3
Juicy Extensions
site:"example[.]com" ext:log | ext:txt | ext:conf | ext:cnf | ext:ini | ext:env | ext:sh | ext:bak | ext:backup | ext:swp | ext:old | ext:~ | ext:git | ext:svn | ext:htpasswd | ext:htaccess | ext:json
High % inurl keywords
inurl:conf | inurl:env | inurl:cgi | inurl:bin | inurl:etc | inurl:root | inurl:sql | inurl:backup | inurl:admin | inurl:php site:example[.]com
Server Errors
inurl:"error" | intitle:"exception" | intitle:"failure" | intitle:"server at" | inurl:exception | "database error" | "SQL syntax" | "undefined index" | "unhandled exception" | "stack trace" site:example[.]com
XSS prone parameters
inurl:q= | inurl:s= | inurl:search= | inurl:query= | inurl:keyword= | inurl:lang= inurl:& site:example.com
Open Redirect prone parameters
inurl:url= | inurl:return= | inurl:next= | inurl:redirect= | inurl:redir= | inurl:ret= | inurl:r2= | inurl:page= inurl:& inurl:http site:example.com
SQLi Prone Parameters
inurl:id= | inurl:pid= | inurl:category= | inurl:cat= | inurl:action= | inurl:sid= | inurl:dir= inurl:& site:example.com
SSRF Prone Parameters
inurl:http | inurl:url= | inurl:path= | inurl:dest= | inurl:html= | inurl:data= | inurl:domain= | inurl:page= inurl:& site:example.com
LFI Prone Parameters
inurl:include | inurl:dir | inurl:detail= | inurl:file= | inurl:folder= | inurl:inc= |inurl:locate= | inurl:doc= | inurl:conf= inurl:& site:example.com
```
**RCE Prone Parameters**
inurl:cmd | inurl:exec= | inurl:query= | inurl:code= | inurl:do= | inurl:run= | inurl:read= | inurl:ping= inurl:& site:example.com
**File upload endpoints**
`site:example.com ”choose file”`
**API Docs**
`inurl:apidocs | inurl:api-docs | inurl:swagger | inurl:api-explorer site:"example[.]com"`
**Login Pages**
`inurl:login | inurl:signin | intitle:login | intitle:signin | inurl:secure site:example[.]com`
**Sensitive Documents**
`site:example.com ext:txt | ext:pdf | ext:xml | ext:xls | ext:xlsx | ext:ppt | ext:pptx | ext:doc | ext:docx`
`intext:“confidential” | intext:“Not for Public Release” | intext:”internal use only” | intext:“do not distribute”`
**Sensitive Parameters**
`inurl:email= | inurl:phone= | inurl:password= | inurl:secret= inurl:& site:example[.]com`
**Adobe Experience Manager (AEM)**
inurl:/content/usergenerated | inurl:/content/dam | inurl:/jcr:content | inurl:/libs/granite | inurl:/etc/clientlibs | inurl:/content/geometrixx | inurl:/bin/wcm | inurl:/crx/de site:example[.]com
**Disclosed XSS and Open Redirects**
`site:openbugbounty.org inurl:reports intext:"example.com"`
**Code Leaks**
`site:pastebin.com "example.com"`
`site:jsfiddle.net "example.com"`
`site:codebeautify.org "example.com"`
`site:codepen.io "example.com"`
**Cloud Storage**
`site:s3.amazonaws.com "example.com"`
`site:blob.core.windows.net "example.com"`
`site:googleapis.com "example.com"`
`site:drive.google.com "example.com"`
`site:dev.azure.com "example[.]com"`
`site:onedrive.live.com "example[.]com"`
`site:digitaloceanspaces.com "example[.]com"`
`site:sharepoint.com "example[.]com"`
`site:s3-external-1.amazonaws.com "example[.]com"`
`site:s3.dualstack.us-east-1.amazonaws.com "example[.]com"`
`site:dropbox.com/s "example[.]com"`
`site:box.com/s "example[.]com"`
`site:docs.google.com inurl:"/d/" "example[.]com"`JFrog Artifactory
site:jfrog.io "example[.]com"
Firebase
site:firebaseio.com "example[.]com"
Dorks that work better w/o domain
Bug Bounty programs and Vulnerability Disclosure Programs
"submit vulnerability report" | "powered by bugcrowd" | "powered by hackerone"
site:*/security.txt "bounty"
Apache Server Status Exposed
site:*/server-status apache
WordPress
inurl:/wp-admin/admin-ajax.php
Drupal
intext:"Powered by" & intext:Drupal & inurl:user
Joomla
site:*/joomla/login
Happy Hacking
Author: Ayush khatkar is a cybersecurity researcher, technical writer and an enthusiastic pen-tester at Asecurity. Contact here.
#bugbounty #infosec #cybersecurity

