Asecurity Top 10 Web Security
Free, online web security blog from the creators of Asecurity
learn about web securityWeb Application Security
introduction
Learn About SQLi
SQL Injection (SQLi) is a prevalent and potent web vulnerability that allows attackers to manipulate a website’s database queries. Imagine a hacker whispering commands directly into the database’s ear, bypassing the website’s security measures and gaining unauthorized access to sensitive information or even control over the entire system. Understanding SQLi:

Learn About Subdomain Takeover
The Art of Hijacking Forgotten Domains Imagine this: You stumble upon a dusty old map leading to a forgotten corner of a vast kingdom. But instead of buried treasure, you find an abandoned castle ripe for the taking. That’s the essence of a subdomain takeover - discovering neglected subdomains and

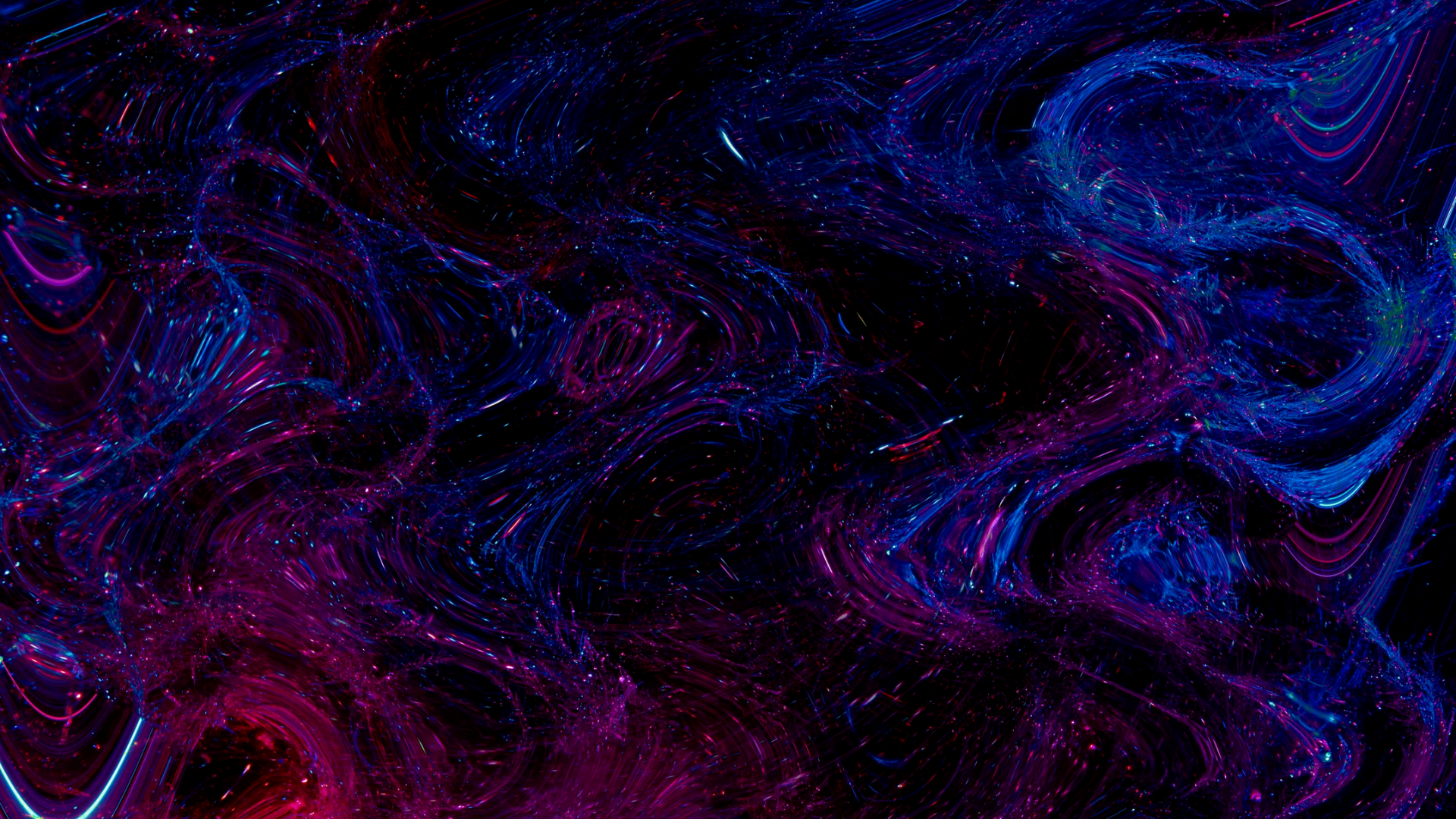
Learn About Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a cunning vulnerability that allows attackers to manipulate a web application into making requests to internal or external resources on their behalf. Imagine a hacker using a web application as a puppet, forcing it to fetch sensitive data or perform actions that it shouldn’t. Understanding
Asecurity Top 100 Ethical Hacking Tools
Free, online Ethical Hacking Tools blog from the creators of Asecurity
learn about ToolsContainers Vulnerability Scanner: Trivy
This article talks about Trivy, which is a simple and comprehensive vulnerability scanner for containers and other artifacts, suitable for Continuous Integration and Testing. Table of Contents * Introduction * Installation * Scanning Git Repository * Scanning Container Image * Scanning Filesystem * Scanning the running Containers * Embed Trivy in Dockerfile Introduction Trivy is an open-source

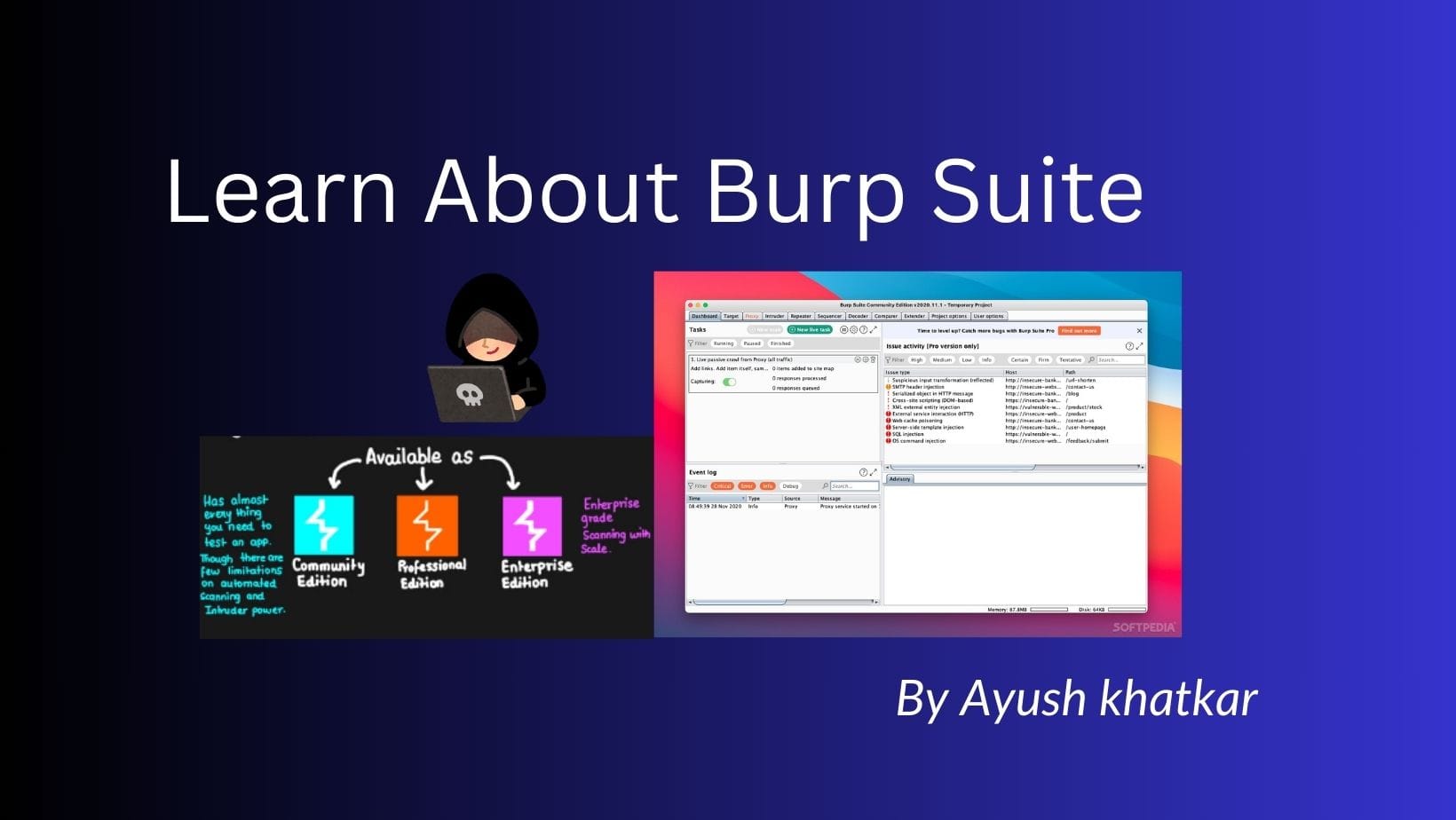
Learn About how to use Burp Suite
Let’s see how to use this Burp Suite stuff and how to make money with it. Installing a browser and proxy: The basics Bug bounty hunters use Burp Suite, a powerful tool, extensively to discover vulnerabilities in web applications. It is a group of technologies that combine to make the
Learn About Google Dork
Google Dork, commonly known as “Google Hacking,” is a method for using Google search to uncover security flaws in a website. Security researchers will find it quite useful, and you may obtain sensitive data, including usernames and passwords, by exploiting Google’s web crawling capabilities. Google Dorks are search terms that


Asecuirty Top 10 API Security Risks
APIs play a very important role in modern application architecture
Learn about APIsExtensive API Pentesting Guide for Bug Bounty Hunters
Introduction APIs (Application Programming Interfaces) are the glue that holds modern applications together. However, they are also a prime target for attackers. A successful API pentest can reveal critical vulnerabilities that could be generously rewarded in Bug Bounty programs. Understanding APIs ● What is an API? An interface that allows different

Broken Authentication in APIs APIs can make you so rich $$$
Introduction Authentication and authorization mechanisms are the gatekeepers of APIs, ensuring that only authorized users can access specific resources and perform allowed actions. However, flaws in these mechanisms are rampant and often lead to severe security breaches. Mastering the art of finding broken authentication vulnerabilities can be a lucrative skill

GraphQL Bugs: Your Hidden Gold in Web Application
GraphQL is a cool new kid on the API block, promising flexibility and efficiency. But guess what? It’s not immune to vulnerabilities, and that’s where we come in – bug bounty hunters! 💰 Why GraphQL? Unlike REST APIs with fixed data structures, GraphQL lets you ask for exactly what you need, kind
Asecurity Top 10 DevSecOps
DevSecOps stands for development, security, and operations
learn About DevSecOpsWhat is DevSecOps? DevSecOps for Beginners
In today’s 1-paced world, software development is all about speed and efficiency. But with increased speed comes increased risk. This is where DevSecOps comes in. What is DevSecOps? Imagine a bakery. They churn out delicious bread, but if they forget to check the ingredients or bake at the wrong temperature,

DevSecOps in Practice: Implementing SAST and DAST
In our previous blog, we introduced the concept of DevSecOps and its importance in building secure software. Now, let’s dive deeper into two essential tools for implementing DevSecOps: Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). Understanding SAST and DAST * SAST (Static Application Security Testing): This method
What is IaC and why it’s important
Deep Dive into IaC Security Understanding Infrastructure as Code (IaC) Infrastructure as Code (IaC) is a revolutionary approach to managing and provisioning IT infrastructure using code rather than manual processes. It involves defining infrastructure resources like servers, networks, and storage in configuration files, which can then be versioned, tested, and


web development
a programmer who develops World Wide Web applications using a client–server model
Learn About Web DevlopmentGetting Started with HTML: A Beginner’s Guide
Welcome back to our web development series! If you’ve already read our first blog post, “Understanding HTML: The Building Blocks of the Web,” you should now have a basic understanding of what HTML is and why it’s essential. In this post, we’ll guide you through setting up your

How to Download and Use VS Code for HTML: A Step-by-Step Guide
Introduction In our previous blog, “Getting Started with HTML: A Beginner’s Guide,” we introduced the basics of HTML and how to begin your journey in web development. Now, let’s dive deeper into setting up a powerful code editor to enhance your HTML development experience. Visual Studio Code (VS Code) is

HTML Tags and Elements: What You Need to Know
HTML (HyperText Markup Language) is the standard markup language used to create web pages. It forms the structure of web pages by using a series of elements, which are represented by tags. Understanding these basic HTML tags and their usage is crucial for anyone beginning their journey into web development.


